A guide for preparing AWS and GCP KMS authentication files.
AWS
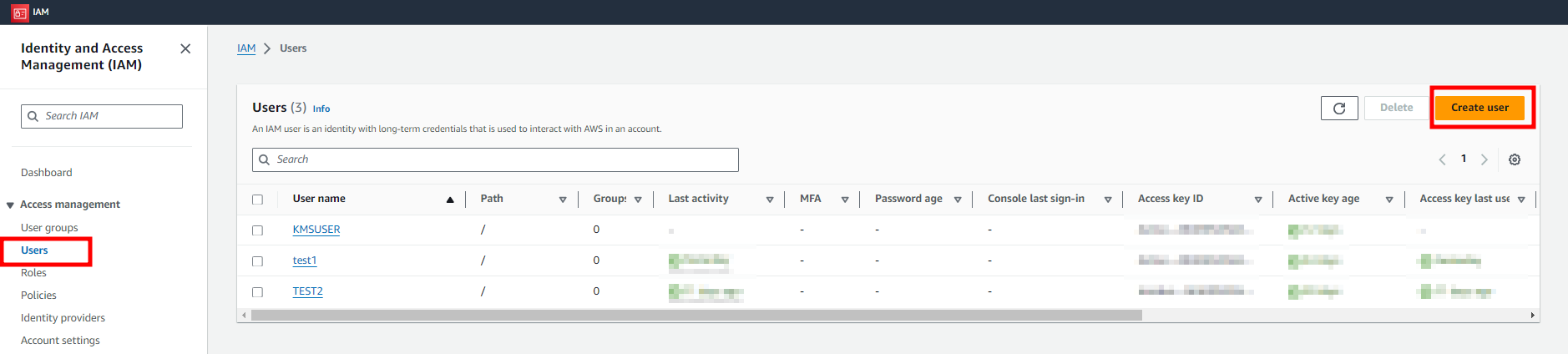
1. Create a user to prepare the AWS authentication file.
- Route : AWS Console > IAM Menu > Users > Create user
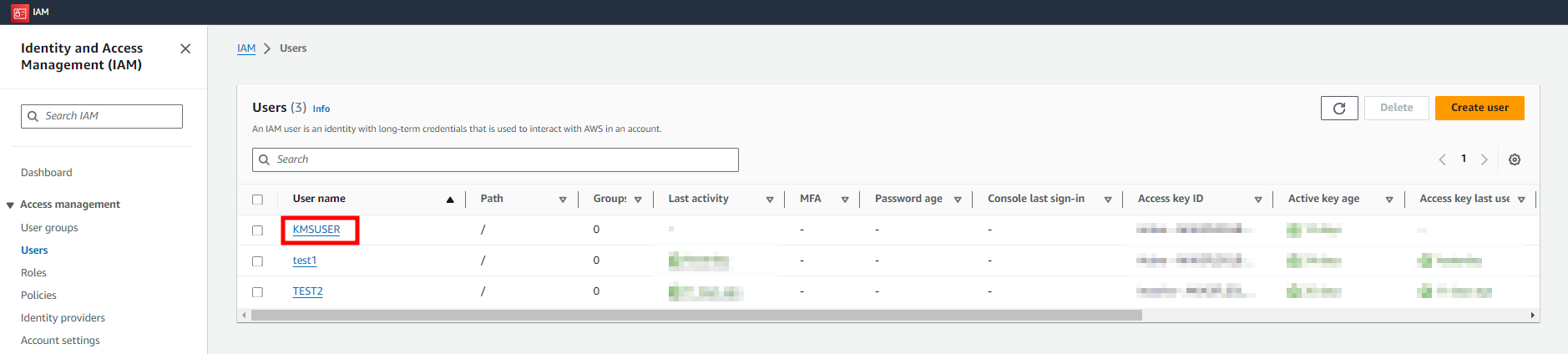
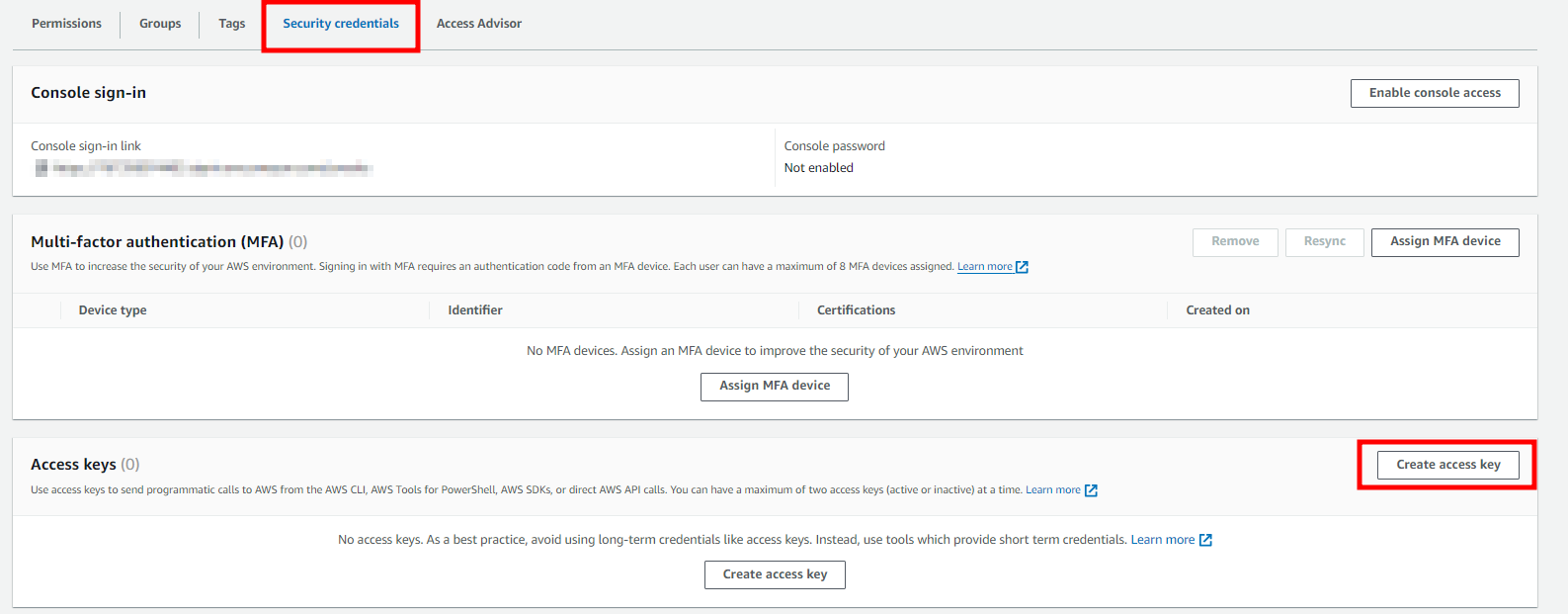
2. Generate an access key.
- Route : Users detail menu > Security credentials > Create access key
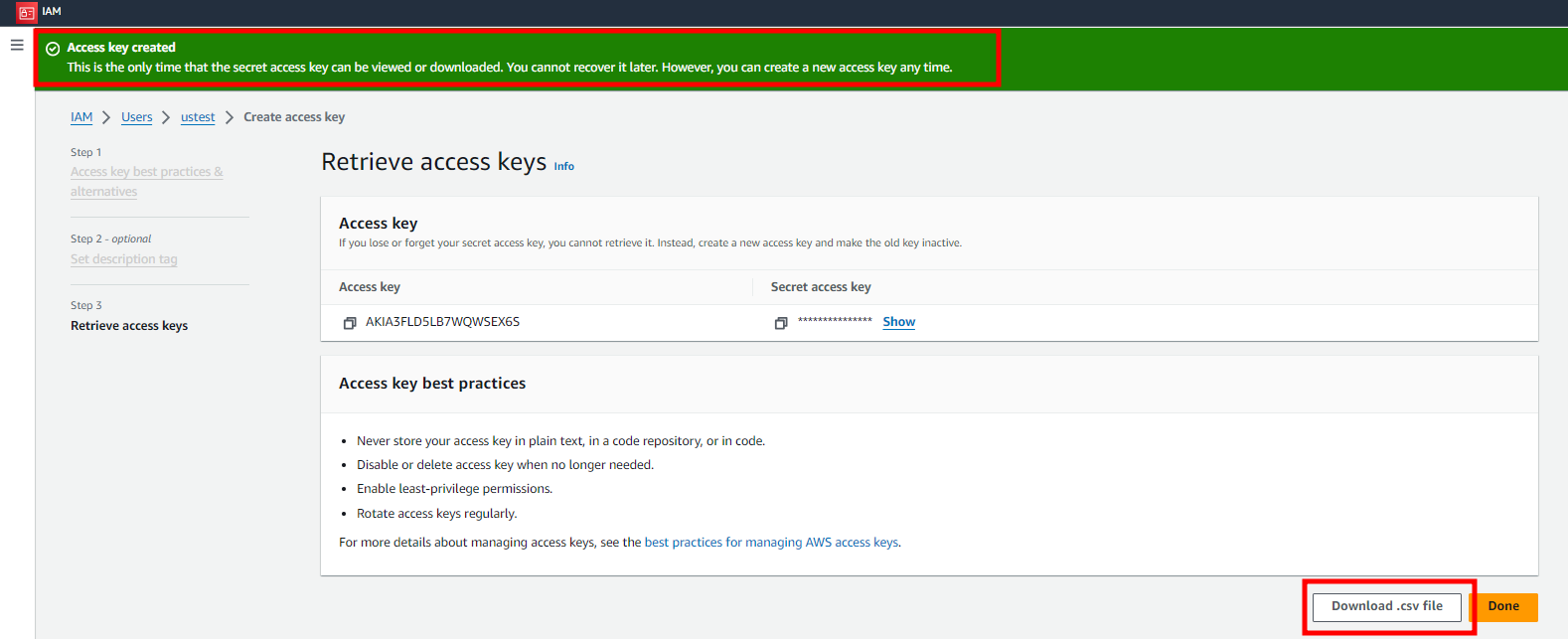
3. After creating the access key, download the CSV file.
- CSV files can only be downloaded once when creating an access key.
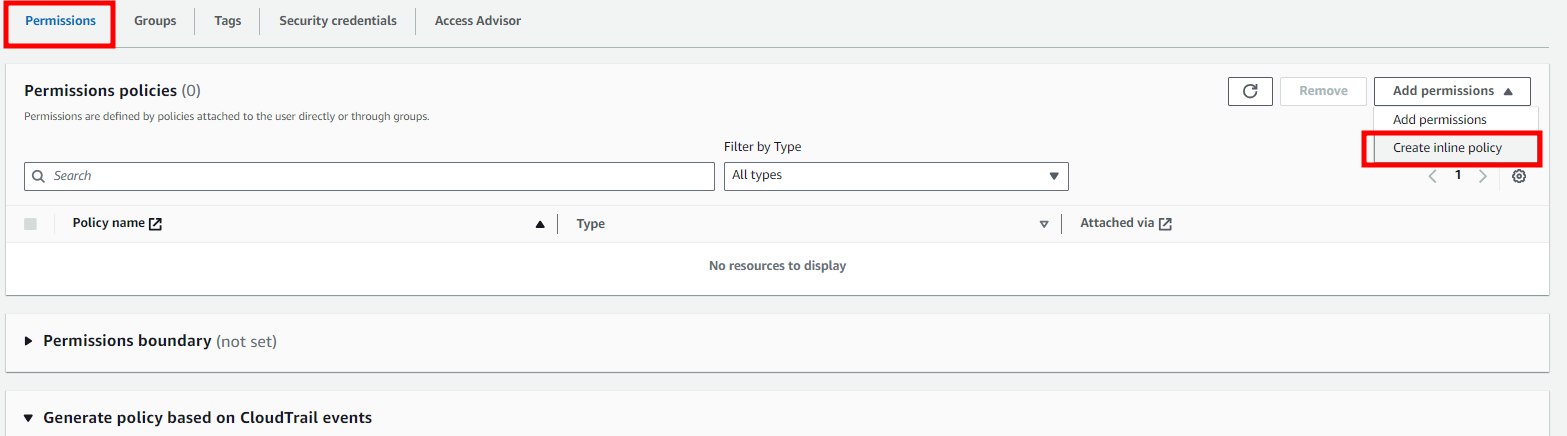
4. Set the permissions required to use the KMS functions.
- Route : Users detail menu > Permissions > Create inline policy
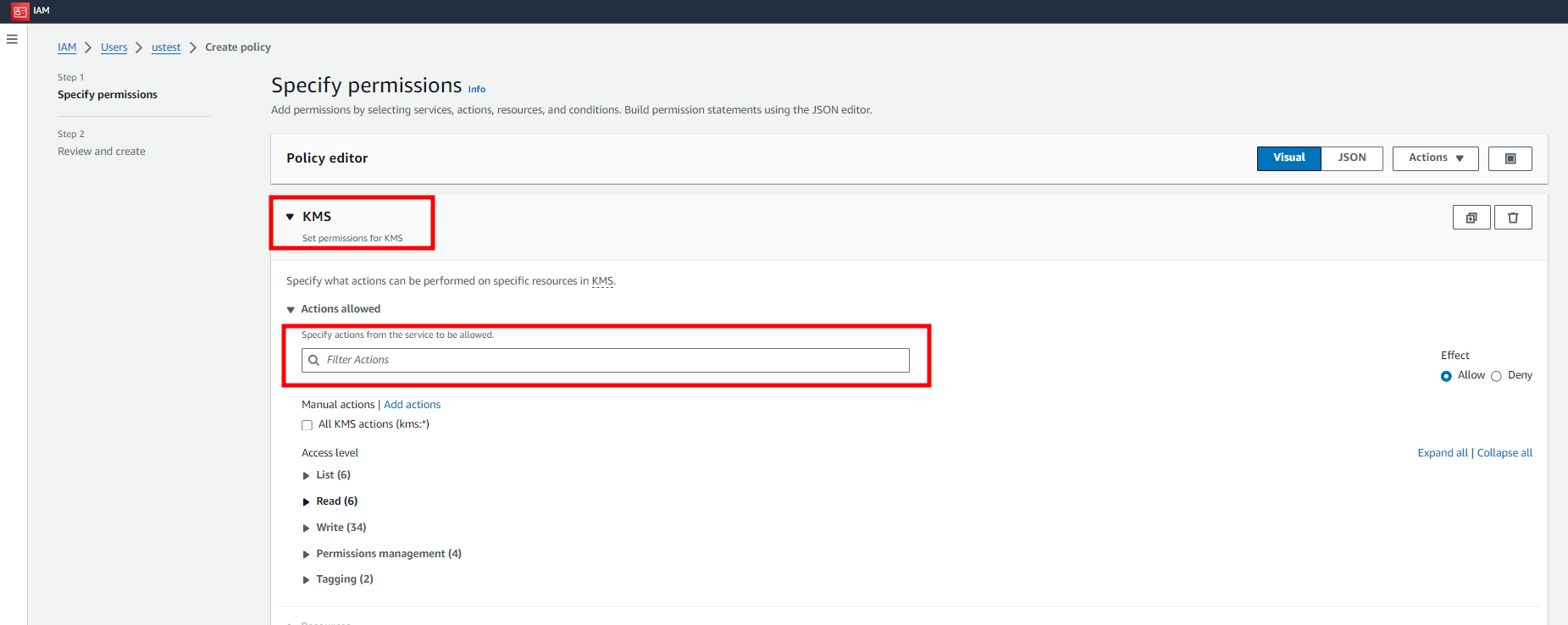
5. Select KMS and add the permissions below manually to complete permission settings.
- kms:CreateKey
- kms:CreateAlias
- kms:DescribeKey
- kms:ListAliases
- kms:GetPublicKey
- kms:Sign
GCP
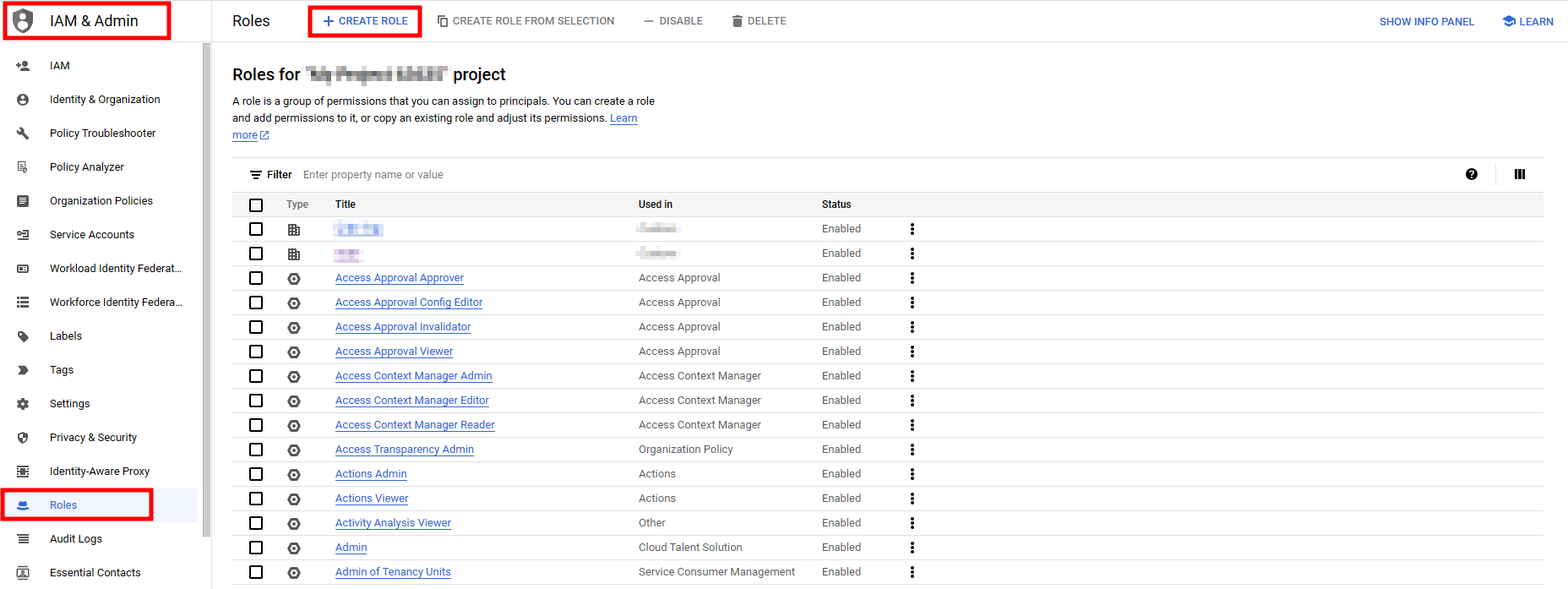
1. Create a role to prepare the GCP authentication file.
- Route : GCP Console > IAM & Admin menu > Roles > Create role
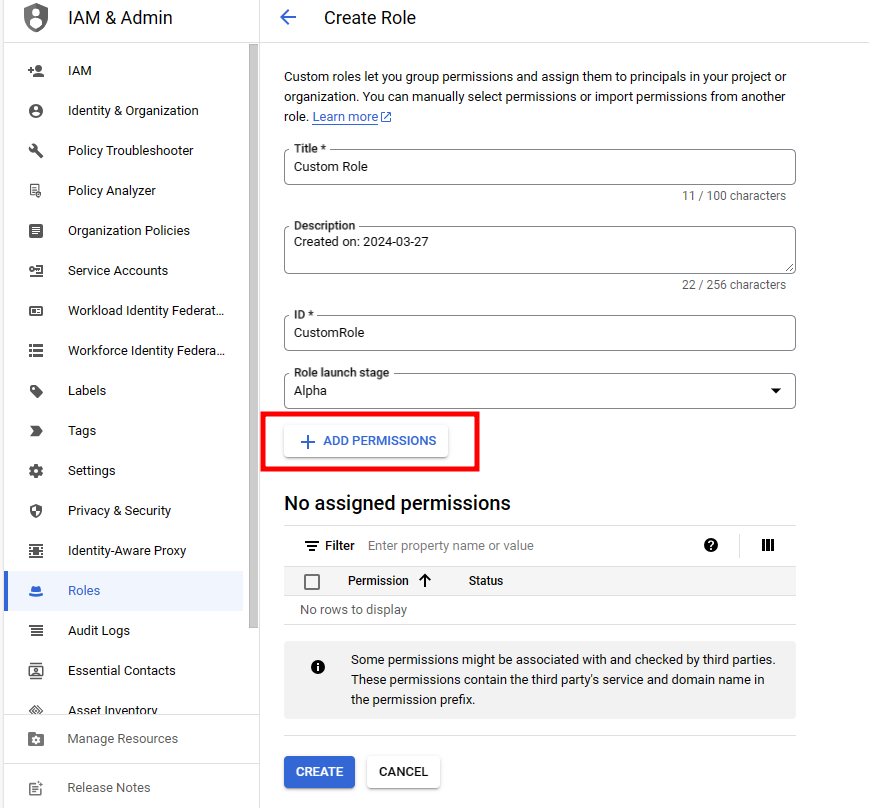
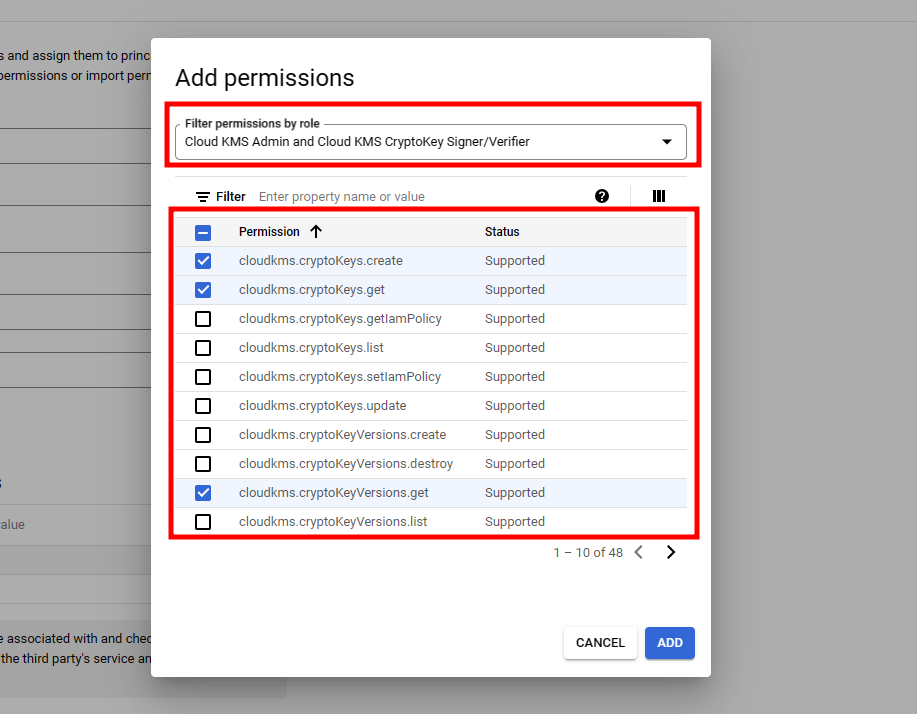
2. Complete the role creation by adding the following permissions required to use the KMS functions.
- cloudkms.cryptoKeys.create
- cloudkms.cryptoKeys.get
- cloudkms.cryptoKeyVersions.get
- cloudkms.cryptoKeyVersions.useToSign
- cloudkms.cryptoKeyVersions.viewPublicKe
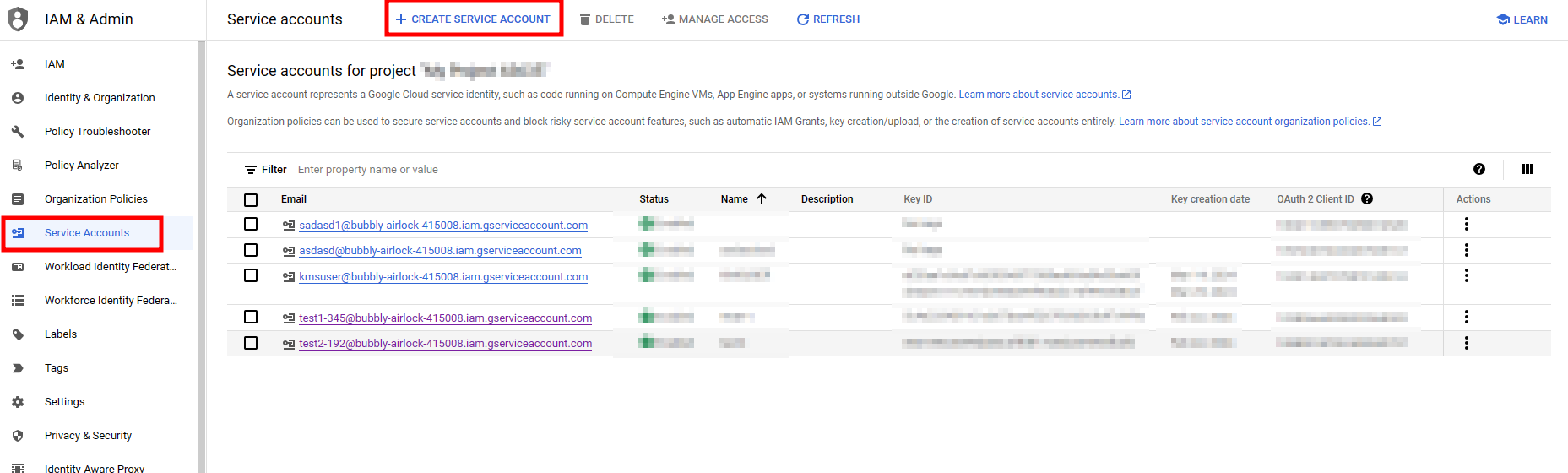
3. Create a service account.
- Route : IAM & Admin menu > Service Accounts > Create service account
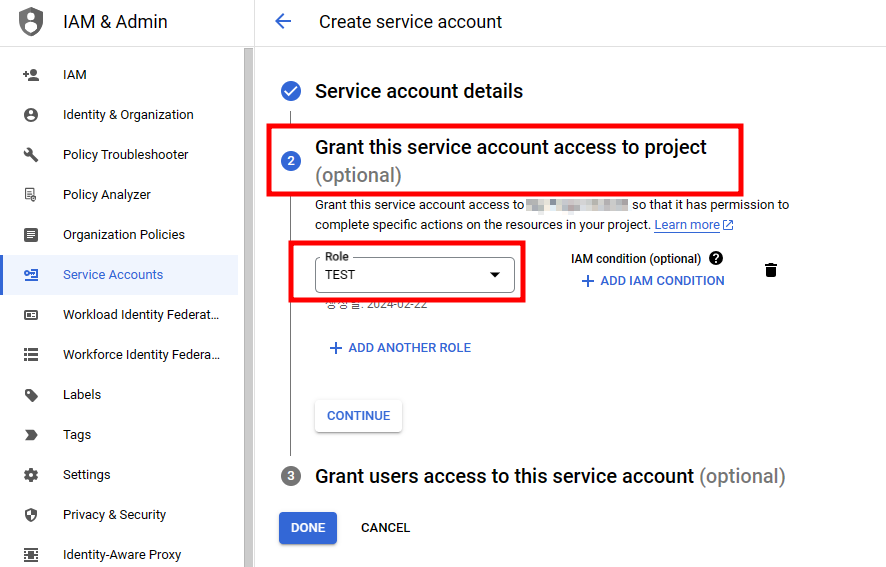
4. Complete the settings for granting access to the service account.
- Route : Create service account > Grant access permission > select the role you created above > complete
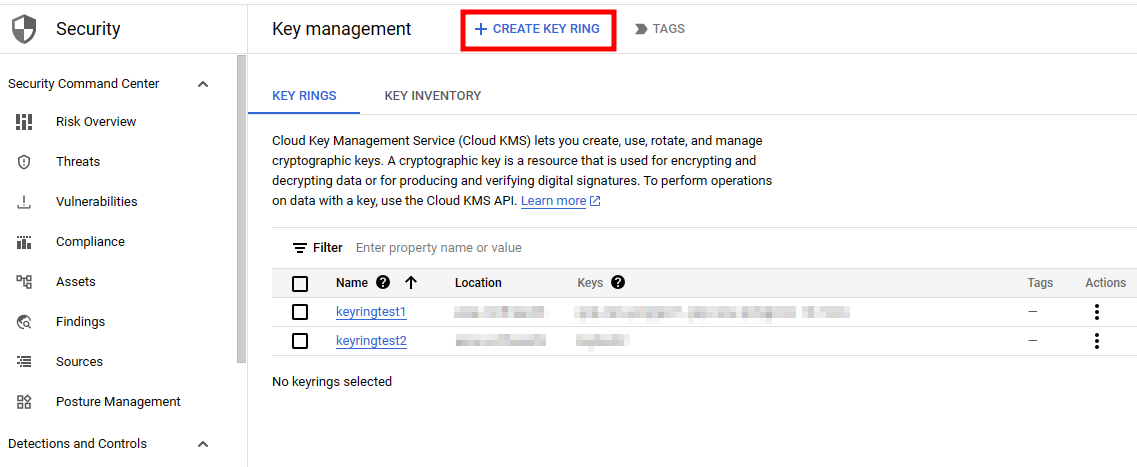
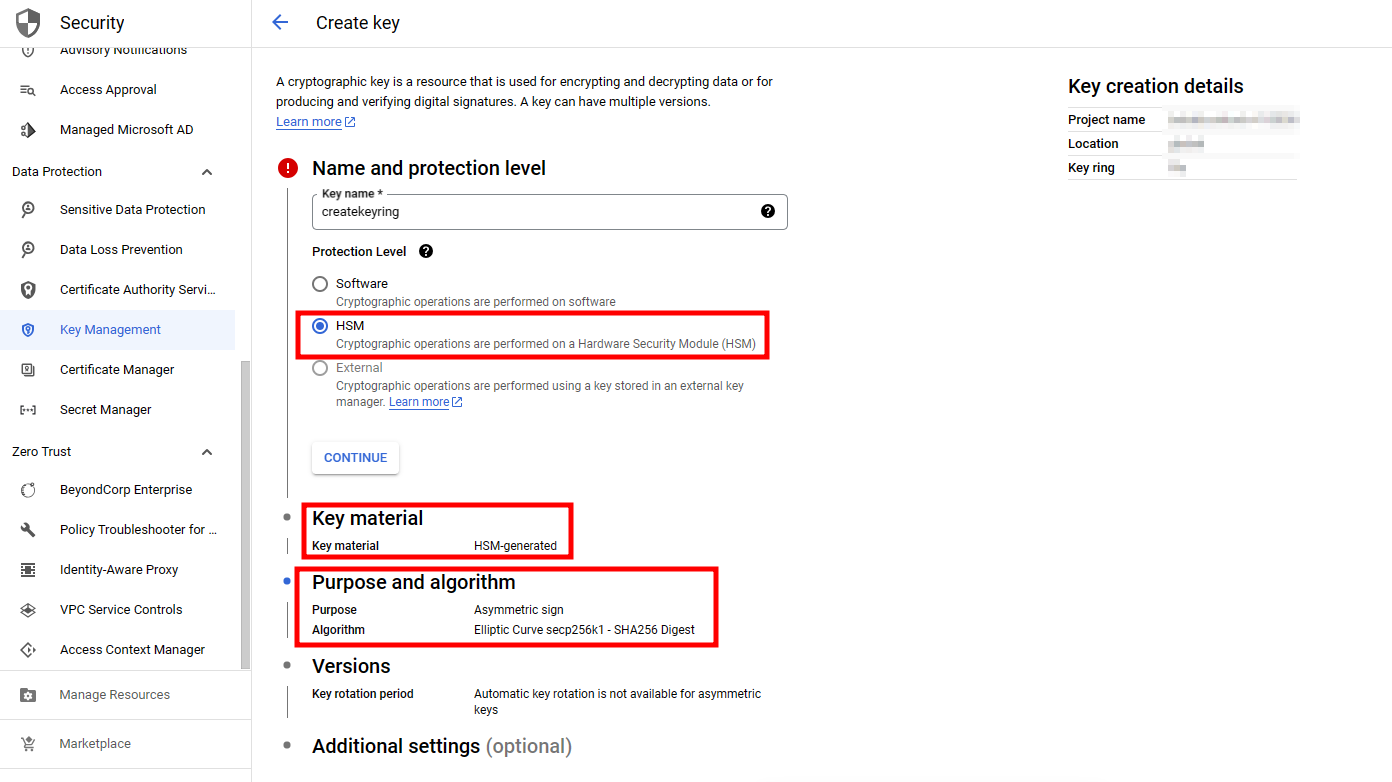
5. Create a keyring (category) to organize multiple keys and control access.
- Route : Security > Key Management > Create key ring
- Name and protection level : HSM
- Purpose and algorithm : Asymmetric sign, Elliptic Curve secp256k1 – SHA256 Digest
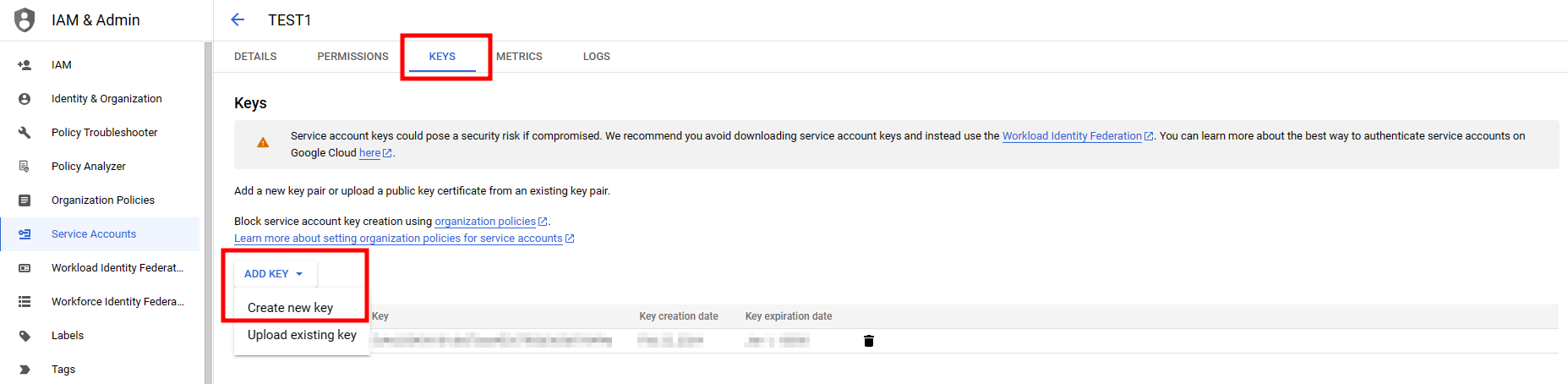
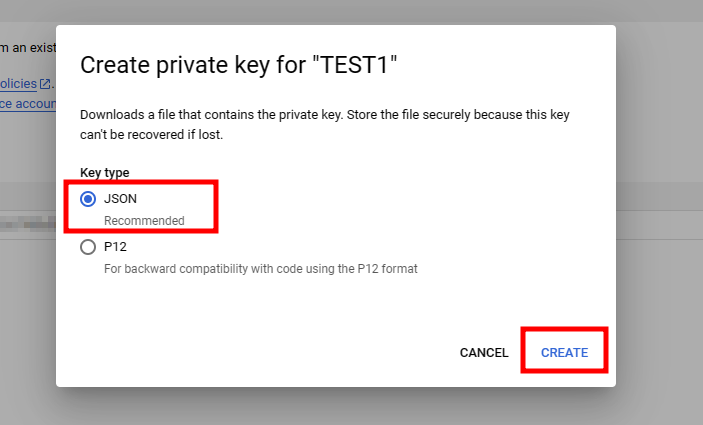
6. Go to the service account details page and create the authentication file in JSON format.
- Route : IAM & Admin menu > Service Accounts > Service Accounts detail info > Keys > Add Key > Create new key